The rollout of 5G networks is transforming the way we connect, offering faster speeds, lower latency, and improved connectivity for devices worldwide. This technology is a game-changer for industries like healthcare, manufacturing, and smart cities. However, as with any technological advancement, 5G introduces several security concerns that must be addressed to ensure safe and reliable communication.
This article delves into the key security concerns of 5G networks, exploring threats such as cyberattacks, data privacy risks, and infrastructure vulnerabilities.
1. Increased Attack Surface Due to Massive IoT Connectivity
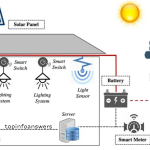
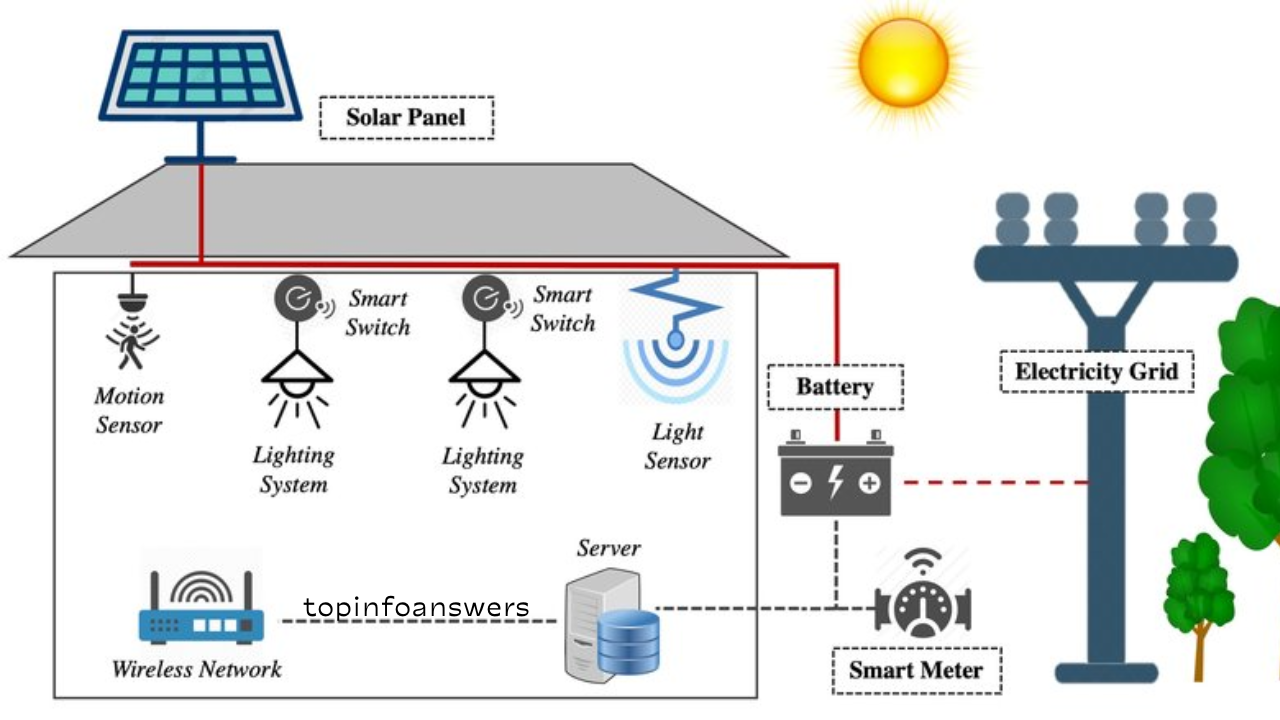
One of the defining features of 5G is its ability to support massive IoT (Internet of Things) connectivity. With billions of devices connecting to the network, security risks grow exponentially. Each connected device represents a potential entry point for hackers.

Key Threats:
- Botnets and DDoS Attacks: Malicious actors can exploit unsecured IoT devices to form botnets and launch Distributed Denial-of-Service (DDoS) attacks.
- Compromised Endpoints: Devices such as smart home gadgets, industrial sensors, and autonomous vehicles could be vulnerable to hacking, leading to system failures and unauthorized data access.
- Lack of Standardized Security Measures: Many IoT devices lack strong encryption and security protocols, making them easy targets for attackers.
2. Network Slicing Vulnerabilities
5G introduces network slicing, which allows operators to create multiple virtual networks tailored for specific use cases. While this increases efficiency, it also introduces new security risks.
Key Threats:
- Cross-Slice Attacks: If one network slice is compromised, attackers may attempt to move laterally across slices, affecting other critical services.
- Data Leakage: Poorly configured slices could lead to unauthorized access and data leaks, particularly in multi-tenant environments.
- Resource Exhaustion Attacks: Attackers could overwhelm specific slices with fake requests, causing performance degradation or network outages.
3. Supply Chain and Infrastructure Security Risks
The 5G infrastructure relies on hardware and software components sourced from various vendors. This supply chain complexity introduces multiple security concerns.
Key Threats:
- Backdoors in Hardware/Software: If compromised components are integrated into the network, they could contain backdoors that allow for surveillance or cyberattacks.
- Vendor Lock-In Risks: Nations relying on foreign technology providers may be susceptible to geopolitical risks and state-sponsored cyber threats.
- Firmware and Software Vulnerabilities: Unpatched vulnerabilities in network equipment can be exploited to disrupt services or steal data.
4. Increased Risk of Cyber Espionage and State-Sponsored Attacks
With 5G supporting critical infrastructure, governments and organizations become prime targets for cyber espionage.
Key Threats:
- Nation-State Attacks: Some governments may exploit 5G networks to conduct espionage, surveillance, and cyber warfare.
- Data Interception: Weak encryption in transit could allow attackers to intercept sensitive information.
- Compromised Base Stations: Malicious actors could target 5G base stations to monitor, manipulate, or disrupt communications.
5. Lack of End-to-End Encryption
While 5G improves encryption compared to 4G, end-to-end encryption (E2EE) is not always enforced.

Key Threats:
- Man-in-the-Middle (MITM) Attacks: Without strong encryption, attackers could intercept communications.
- Data Tampering: Weak security configurations could allow bad actors to modify messages in transit.
- Privacy Concerns: Lack of encryption could expose user locations, personal data, and sensitive communications.
6. Authentication and Identity Management Challenges
5G networks require robust authentication mechanisms to prevent unauthorized access. However, several vulnerabilities exist in this area.
Key Threats:
- SIM Card Cloning: Attackers can clone SIM cards to impersonate legitimate users.
- Unauthorized Network Access: Poorly implemented authentication methods could allow adversaries to gain access to critical network functions.
- Insider Threats: Malicious insiders within telecom companies or service providers could exploit weak identity management systems to access confidential information.
7. Threats to Critical Infrastructure
5G is set to play a crucial role in powering critical infrastructure such as smart grids, transportation, and emergency services.
The Role of 5G in Enabling Virtual Reality (VR) and Augmented Reality (AR)
Key Threats:
- Power Grid Attacks: A compromised 5G network could be used to disrupt power supply systems.
- Autonomous Vehicle Hacking: Connected vehicles relying on 5G could be hacked, leading to accidents or unauthorized control.
- Healthcare System Breaches: Attackers could manipulate medical devices and patient data, endangering lives.
8. Regulatory and Compliance Challenges
Different countries have varying regulatory standards for 5G security, making it challenging to enforce uniform protection measures.
Key Challenges:
- Lack of Global Security Standards: The absence of universally accepted security regulations leads to inconsistent implementations.
- Data Sovereignty Issues: Governments may impose data localization laws, creating challenges for cross-border data protection.
- Telecom Provider Compliance: Network providers must comply with strict cybersecurity regulations, increasing costs and complexity.
9. AI and Machine Learning-Based Threats
While Artificial Intelligence (AI) and Machine Learning (ML) enhance 5G security, they can also be exploited by attackers.

Key Threats:
- AI-Powered Cyberattacks: Hackers can use AI to develop sophisticated attacks, such as automated phishing or intelligent malware.
- Deepfake and Spoofing Attacks: AI-generated deepfake audio or video could be used for fraudulent activities.
- Data Poisoning Attacks: Adversaries could manipulate ML models used in 5G network security systems, rendering them ineffective.
Mitigation Strategies for 5G Security Concerns
To counter the security risks associated with 5G, organizations and governments must adopt proactive security measures.
Key Solutions:
- Zero Trust Architecture: Implementing a zero-trust security model ensures that no device or user is trusted by default.
- Strong Encryption and Authentication: Enforcing end-to-end encryption and multi-factor authentication (MFA) reduces risks.
- Continuous Monitoring and AI-Based Threat Detection: Using AI-driven cybersecurity tools to detect anomalies and threats in real time.
- Secure Supply Chain Management: Governments and telecom providers should ensure trusted vendors and secure firmware updates.
- Regulatory Compliance and Global Cooperation: Establishing international cybersecurity standards for 5G to ensure consistent protection across borders.
While 5G technology brings unparalleled speed, efficiency, and connectivity, it also introduces significant security challenges that must be addressed. From IoT vulnerabilities and cyber espionage to network slicing risks and critical infrastructure threats, securing 5G networks requires a multi-layered approach.
By implementing robust security measures, enforcing global regulatory compliance, and leveraging AI-driven cybersecurity, we can mitigate these threats and ensure a safe, resilient, and secure 5G future.
5G and AI: How These Two Technologies Will Transform the World
As 5G adoption continues to grow, staying ahead of emerging threats will be crucial in protecting users, businesses, and nations from potential cyber risks.